If you’re interested in the security at the root of DNSSEC, you can watch the IANA DNSSEC Root KSK Ceremony streaming live today – happening right now, in fact – from a data center in Culpeper, Virginia. Just go to:
https://icann.adobeconnect.com/kskceremony
where you can connect to ICANN’s Adobe Connect streaming service. There you can watch as the participants work their way through the 56-page script for today’s key ceremony.
 The key ceremony today began at 1:00pm US EDT (17:00 UTC) and will end at 5:00pm EDT (21:00 UTC).
The key ceremony today began at 1:00pm US EDT (17:00 UTC) and will end at 5:00pm EDT (21:00 UTC).
The key ceremonies are part of the activities performed by the Internet Corporation for Assigned Names and Numbers (ICANN) under its contract to operate the Internet Assigned Numbers Authority (IANA). As explained on the overview page:
Ceremonies are usually conducted four times a year to perform operations using the Root Key Signing Key, and involving Trusted Community Representatives. In a typical ceremony, the KSK is used to sign a set of operational ZSKs that will be used for a three month period to sign the DNS root zone. Other operations that may occur during ceremonies include installing new cryptographic officers, replacing hardware, or generating or replacing a KSK.
This ceremony today is to use the “master” root Key Signing Key (KSK) to generate a set of Zone Signing Keys (ZSKs) that will then be used until the next key ceremony. The “root key” is at the top of the “global chain of trust” that is used to ensure the correct validation of DNSSEC signatures (for more info see “The Two Sides of DNSSEC“) and so it is critical that the security and integrity of this root key be maintained. Ceremonies such as the one today are a part of that effort. If you are interested in learning more, today is a bit of a peek behind the curtain about how all of this happens.
This ceremony will be a bit different from other ones in that they will actually be replacing the Hardware Security Modules (HSMs) that are used to store the actual private key of the Root KSK. This process was explained in detail in a March 2015 blog post: ICANN Announces 2015 Hardware Security Module Replacement Project for the Root Key Signing Key. For those curious, the HSM replacement process starts on page 19 of today’s ceremony script.
Now, granted, occasionally watching people enter commands into a Linux command prompt may not necessarily be as exciting as watching rockets launch…
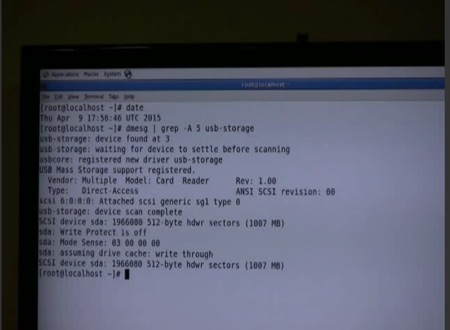
… but it’s still rather cool that we get to watch the whole process unfold remotely!
And… it’s much more than the command-line operations… you are also getting to see some of the people who hold parts of the keys at the root of DNSSEC do their parts in the actual ceremony. Some of them you may recognize from when we’ve written about them or from some of the articles they written or presentations they’ve made.

You also get to see some of the steps of the process up close:

If you can’t watch it live, it is being recorded and you can always go back and view it.
P.S. If you want to learn more about how to get started with DNSSEC, please visit our “Start Here” page to find resources focused on your type of role or organization.
