We are acutely aware of how the Internet impacts and transforms the world. It has the ability accelerate human progress, bridge the digital divide and build societies that drive innovation, entrepreneurship, and progress.
Today we are at a defining moment in the evolution and growth of the Internet.
Large-scale data breaches, uncertainties about the use of our data, cybercrime, surveillance and other online threats are eroding users’ trust and affecting how they use the Internet. Eroding trust is also affecting the way governments view the Internet, and, is shaping the policy environment for the Internet around the world..
We face a situation where we risk undoing all of the progress we have made over the past three decades.
It is time to act.
In the 2016 Global Internet Report, we take a close look at data breaches, offer approaches to help prevent them, and how these measures will positively impact user trust and the global digital economy.
We approach the issue through an economic lens, and ask the hard question: Why are organisations not taking all available steps to protect those who entrust them with their personal information? We also explore market failures and their impact on organisations’ data security.
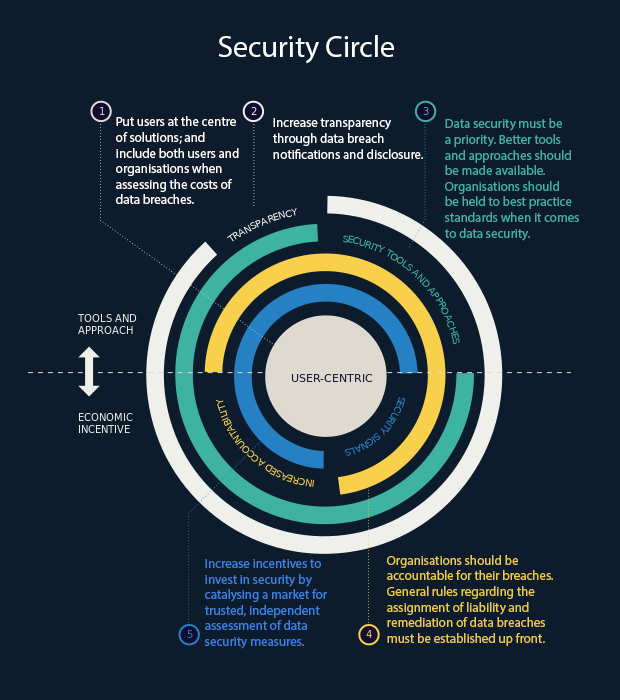
We provide five clear recommendations for a path forward to address the increasing incidence and impact of data breaches.
Report Highlights
- Data and Trends (pg.31)
- Case studies (pg.67)
- Issues (pg.91)
- Recommendations (pg.111)
Executive Summaries
The following executive summaries are now available for download:
