Apple recently announced some major changes to their operating systems across all platforms during their flagship developer conference WWDC. The Worldwide Developers Conference is where developers can attend sessions and meet with over 1,000 Apple engineers, and this event included a keynote introducing new software (iOS 11, macOS High Seirra and watchOS 4) and hardware (iPad Pro and HomePod) . The 2017 conference was held 5-9 June in San Jose, California, and apart from the other announcements, there are two major developments in the networking area.
- Support of MPTCP (Multi Path TCP)
- Support of TLS 1.3
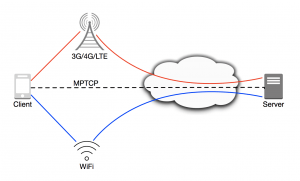 MPTCP (Multi Path TCP) is defined by RFC6824, and has the ambition of enabling the simultaneous use of several IP-addresses/interfaces by modifying TCP to present a regular TCP interface to applications, whilst in fact sending data over several subflows. The benefits include better resource utilization, better throughput and redundancy. Apple has been using MPTCP for their Siri application since the release of iOS 7 in 2013, and according to the statistics presented during the WWDC – Advances Networking event, they have seen 20% (95th Percentile) faster user feedback and a 5 times reduction in network failure.
MPTCP (Multi Path TCP) is defined by RFC6824, and has the ambition of enabling the simultaneous use of several IP-addresses/interfaces by modifying TCP to present a regular TCP interface to applications, whilst in fact sending data over several subflows. The benefits include better resource utilization, better throughput and redundancy. Apple has been using MPTCP for their Siri application since the release of iOS 7 in 2013, and according to the statistics presented during the WWDC – Advances Networking event, they have seen 20% (95th Percentile) faster user feedback and a 5 times reduction in network failure.
Apple considers this a great success and in iOS 11 they are opening up the API for MPTCP which they have specifically been using for Siri until now. This requires server support as well, but the good news is that many load balancers already support it, and whilst the main linux kernel doesn’t currently support it, a new kernel with MPTCP support is available from INL (IP Networking Lab, UCL – Belgium). AWS and GCE images are also available, whilst Android images are available for 4.4.x only. Geoff Huston (APNIC) has written a detailed blog on MPTCP.
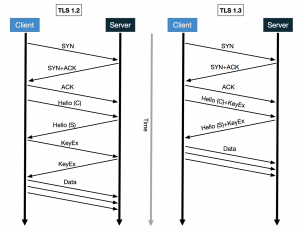
TLS 1.3 (Transport Layer Security) – The underlying technology that enables secure communication on the Internet is a protocol called Transport Layer Security (TLS), which is an evolution of Secure Sockets Layer (SSL) developed by Netscape in the 1990s. TLS 1.0 was first defined in RFC 2246 in January 1999 as an upgrade of SSL Version 3.0, and was updated with TLS 1.1 that was defined in RFC 4346 in April 2006. The most recent version, TLS 1.2, was standardized in RFC 5246 in 2008, and is currently supported by the majority of browsers and HTTPS-enabled web services. All TLS versions were further updated in RFC 6176 in March 2011, removing their backward compatibility with SSL so that TLS sessions will not negotiate the use of Secure Sockets Layer (SSL) version 2.0.
TLS 1.3 currently in its draft stage, and was first announced in April 2014. Since then it has undergone many changes, but is expected to become an Internet standard by the end of this year. TLS 1.3 has two main advantages over previous versions:
- Enhanced security
- Legacy options, ciphers, and key exchange algorithms removed
- TLS 1.2 features that have been removed were associated with high profile attacks in the past
- Improved network efficiency
TLS 1.3 is not enabled by default in iOS 11, but is a huge step forward for web security and performance. Apple also announced support for ECN (Explicit Congestion Notification) during their Advances in Networking session. If you want to check out other announcements, then you can find all the other sessions online.
- Network Session: Advances in Networking Part 1 and Part 2
- Security Session: Your Apps and Evolving Network Security Standards
Deploy360 also aims to help this process, so please take a look at our TLS section to understand why the use of TLS is important.