Securing
Global Routing
The world needs a secure and resilient Internet.
Without taking steps to protect the global routing system, it’s prone to leaks and other errors, as well as hijacks from nefarious actors. These can lead to misdirection of traffic and denial of service, damaging reputations, causing lost revenue, and exposing sensitive data.
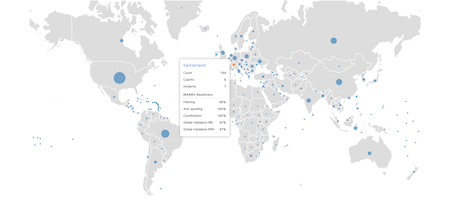
Mutually Agreed Norms for Routing Security (MANRS) is an industry-supported initiative that builds on well-established best practices by bringing together actions that can address the most common threats in the global routing system. By adopting MANRS, network operators and others can help make sure information—from email to streaming videos—arrives at its intended destination. We need MANRS for the global security of everything that travels via the Internet.
Defending the Internet
Because secure global routing is the bedrock of a trustworthy Internet, we’re:
- Continuing to operate MANRS training programs.
- Remaining active in the MANRS community and advocating for increased routing security.
Get Involved


Latest News
Image copyright:
© Nyani Quarmyne, © Gagny Traoré